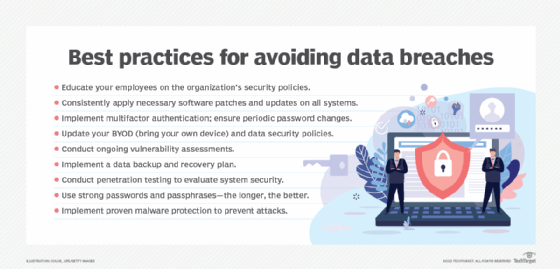
14) which of the following are breach prevention best practices
In the age of digital data keeping information safe is more important than ever. What is a major security breach.
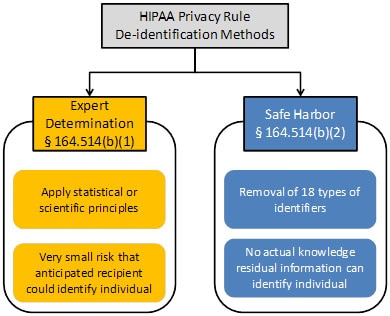
Methods For De Identification Of Phi Hhs Gov
The following are high-level best practices for preventing breaches.

. A security breach is any incident that results in unauthorized access to computer data applications networks or devices. 11 Which of the following are breach prevention best practices. In which of the following circumstances must an individual be given the opportunity to agree or object to the use and disclosure of their PHI.
Phases of a data breach reported data breaches data breach laws best practices. Which of the following are breach prevention best practices. Developing the IRP will help the IT staff of the company to control the data breach incidents.
Best Practices For Prevention And Immediate Response To A Breach. Identify areas that store transmit collect or process. Which of the following are examples of personally identifiable information PII.
Which Of The Following Are Breach Prevention Best Practices. 2 data breach landscape data breaches cost companies an average of 221 per. Which of the following are breach prevention best practices.
Which are breach prevention best practices. Properly configure the cloud. HIPAA and Breach Prevention.
Protects electronic PHI ePHI c. Identity sensitive data collected stored transmitted or processes. The following are high-level best practices for preventing breaches.
30 Best Practices for Preventing a Data Breach. Which of the following are breach. In which of the following.
Breach prevention strategies TheftLoss. Which of the following are breach prevention best practices. Invest in security automation.
Access only the minimum amount of PHIpersonally identifiable information PII necessary Logoff or lock your. Attracting new customers or regaining the loyalty of existing customers following a successful and widely publicized breach is very. The employees play an essential responsibility in keeping their companies safe.
This was a result of 2935 data breaches. All of this above. Implementing encryption standards and backup policies to decrease risks and make sure that software is up-to-date and.
Companies that leveraged artificial intelligence machine learning. Create Strong Policies Strong Passwords. Companies take steps to apply data.
Awasome 14 Which Of The Following Are Breach Prevention Best Practices 2022. Invest in security automation. A breach as defined by the DoD is broader than.
Vulnerability assessment is the process intended to identify classify and prioritize security threats and. Making weak passwords can be a reason for Data. Which of the following statements about the HIPAA Security Rule are.

Cybersecurity Best Practices For 2022 15 Data Protection Methods Ekran System

Top 10 Zero Day Attack Prevention Best Practices 2022 Cybertalk

Cyber Resilience Security Insider
![]()
How To Quantify The Cost Of A Data Breach A Case Study

Securitymetrics Guide To Hipaa Compliance

What Is Extended Detection And Response Xdr Definition Components Advantages And Best Practices Spiceworks It Security

Best Practices To Protect Your Business Email
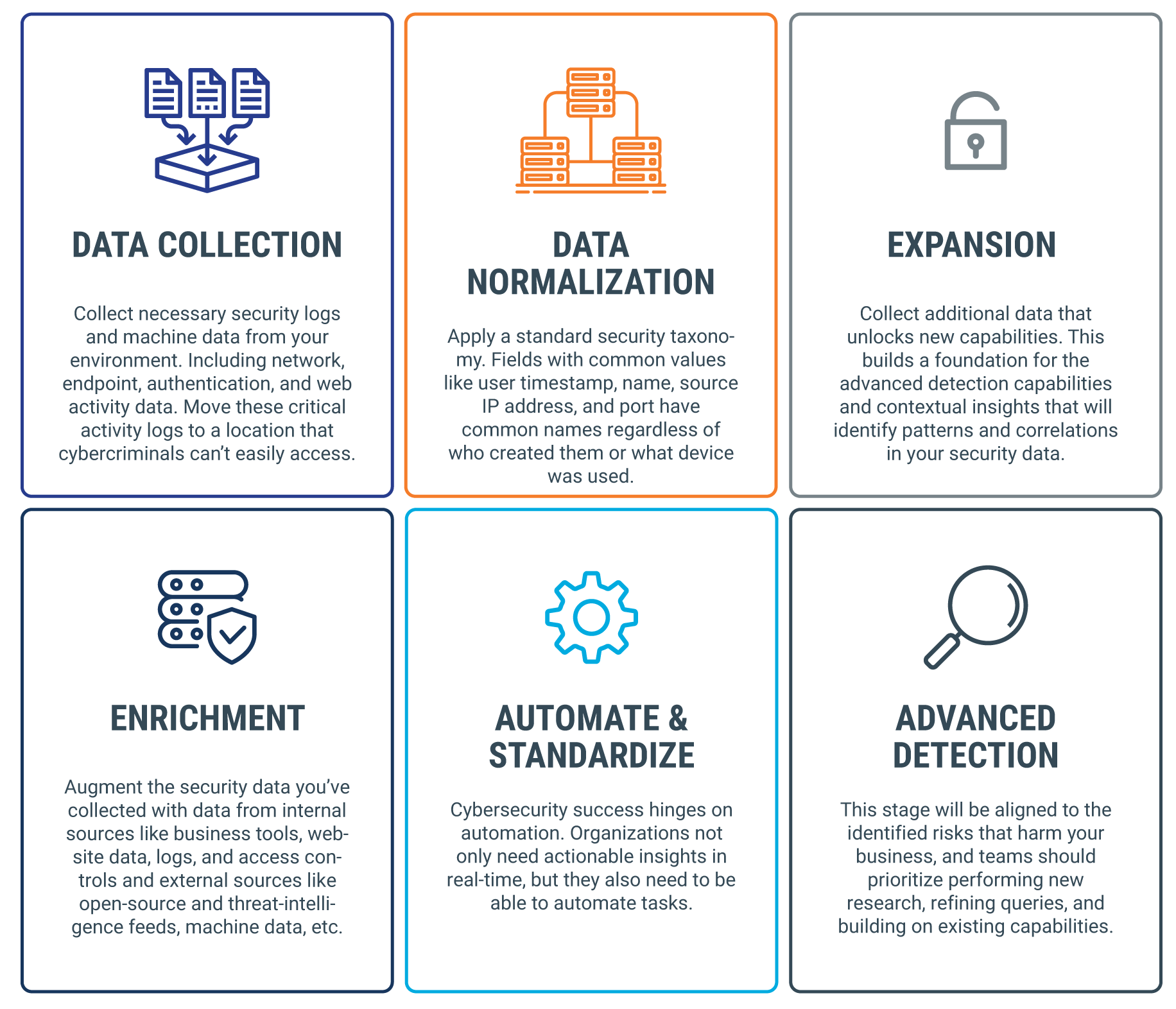
Data Analytics Cybersecurity Best Practices 3pillar Global

30 Best Practices For Preventing A Data Breach Securityscorecard

6 Most Common Causes Of Data Leaks In 2022 Upguard
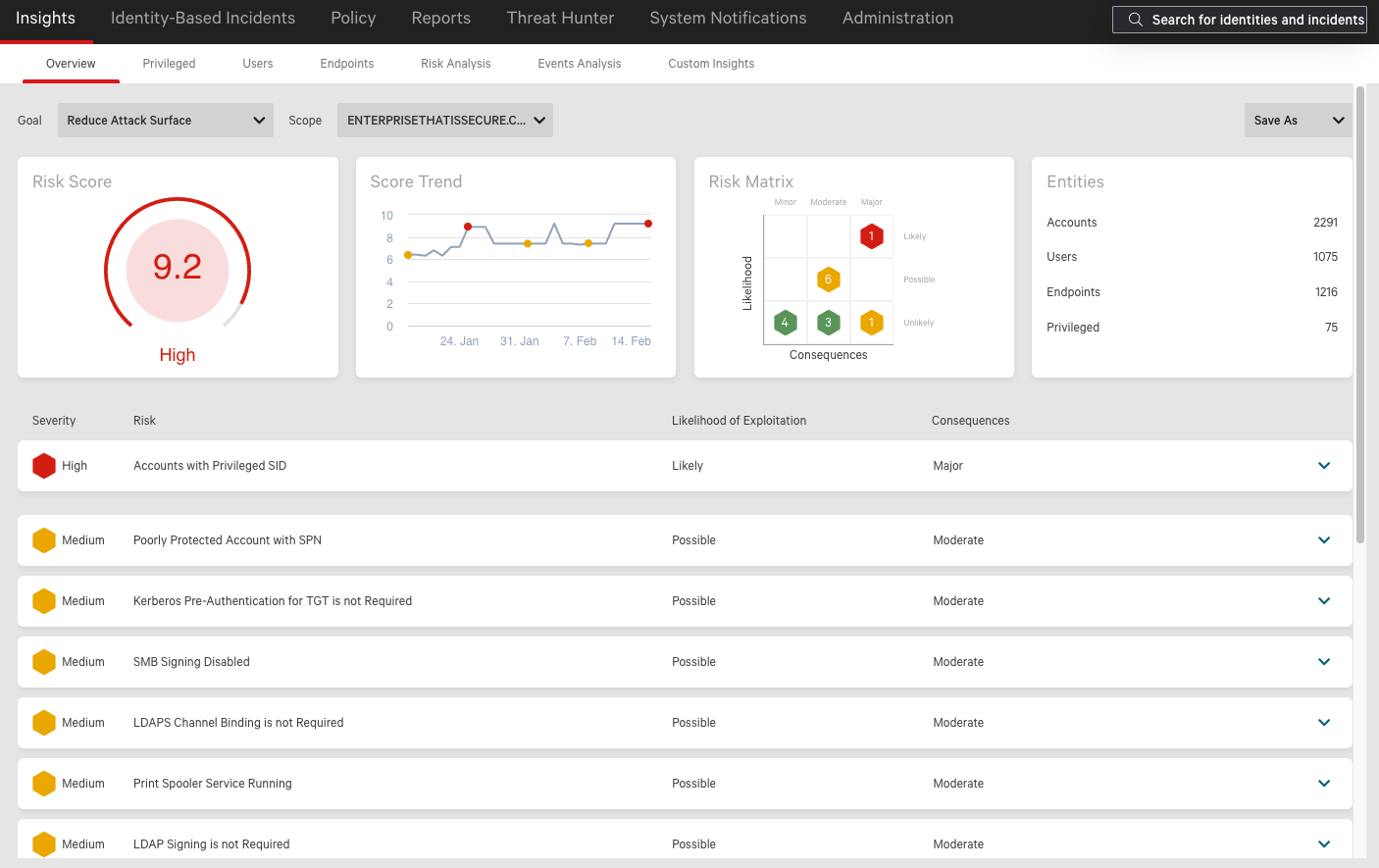
Crowdstrike Falcon Elite Advanced Breach Prevention
5 Best Practices For Data Breach Prevention Endpoint Protector

Cybersecurity Best Practices For 2022 15 Data Protection Methods Ekran System
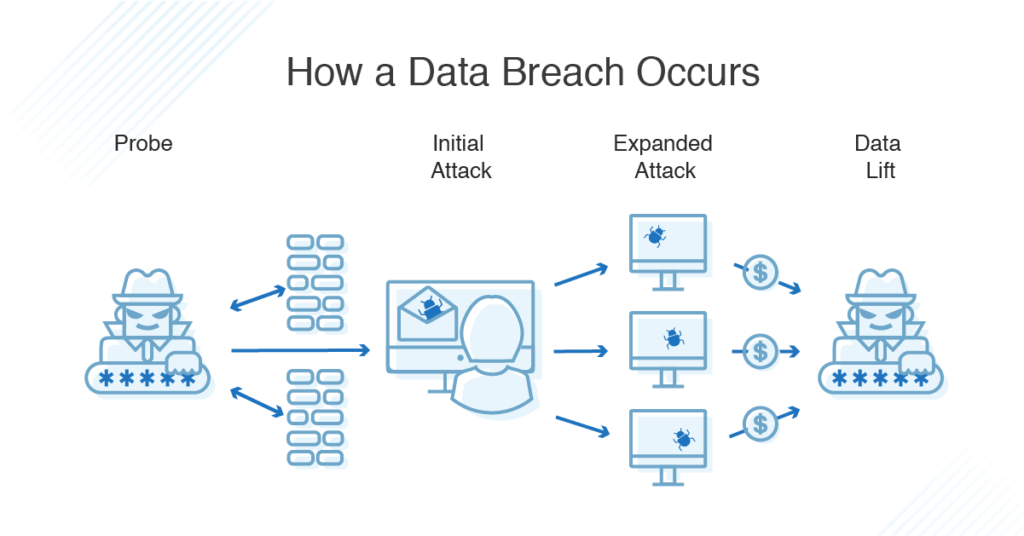
What Is A Data Breach Definition Types Dnsstuff

Hippa Docx Contains 20 Questions Attempt 1 2 Challenge Exam 1 In Which Of The Following Circumstances Must An Individual Be Given The Course Hero

Which Of The Following Are Breach Prevention Best Practices All Of The Above You Course Hero
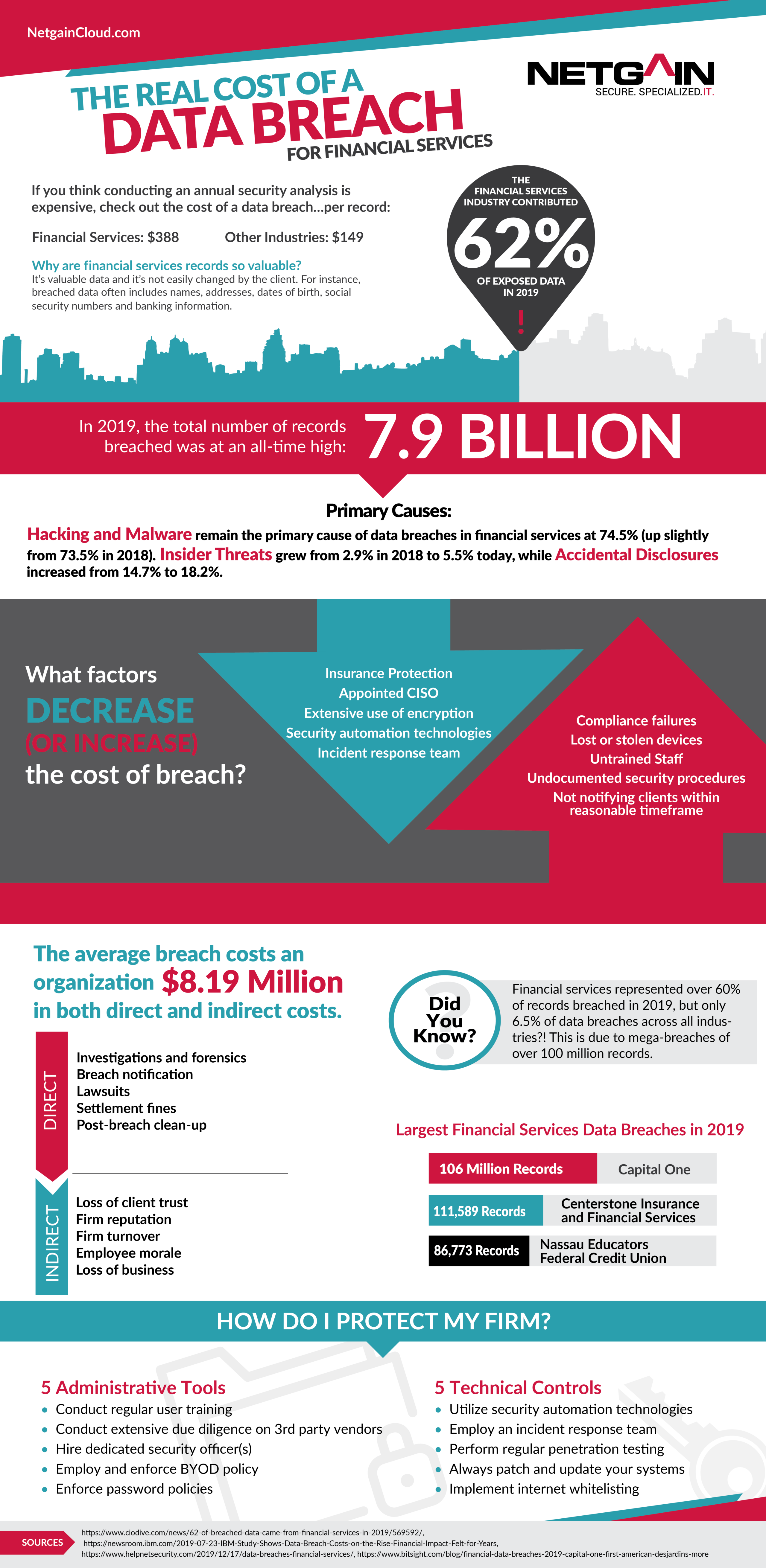
How Costly Is A Data Breach Netgain

Preventing Data Breaches Starts With Creating And Training On Policies